You may have heard someone say that they use a VPN to protect themselves on the internet. What is a VPN? What does it do? How can you use it to protect yourself?
VPN stands for virtual private network. They are essentially simulations of connections (hence the ‘virtual’ part) to a certain private networks (networks that one can’t normally connect to from outside or over the internet). They allow users to connect to a local private (e.g. corporate) network remotely from, say, their home, or a coffee shop. A VPN allows its users to interact with the local network as if they were normally connected to it. For example, say a developer at a tech startup wanted to work on her project at her local Starbucks instead of commuting into the office, but to protect their intellectual property the startup doesn’t allow anyone to look at their code without being connected to their local onsite network (sometimes referred to as an intranet). However, the developers at the startup aren’t big fans of the cubicle life, and like to roam around and do their work at the library with a book, or at home with their dogs. Fortunately, the startup has a VPN set up so that the developers can log into the intranet and look at their projects remotely. The computer appears as if it actually is physically located in the office and has almost all of the access that it would have if it was literally in the office.
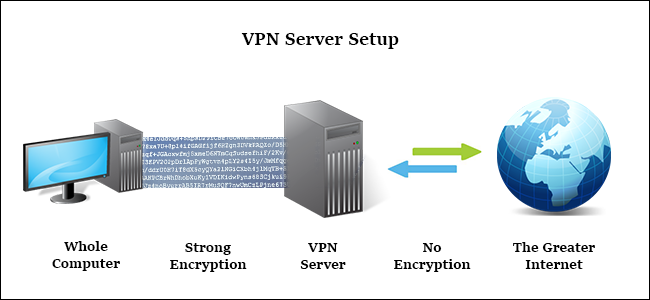
But how does the VPN make sure that only the right people have access to the network? This is where the magic of the VPN is. When you log into your VPN client with your username and password and the server authenticates you, your computer creates a point-to-point encrypted tunnel between you and the VPN server — think of it as a really long tube that runs between your computer and the server in the office that nobody in between can look inside of. That means if you’re sitting at Starbucks and your company uses Comcast as its internet service provider, nobody in your Starbucks can peek into your Wi-Fi signal (this is referred to as a man-in-the-middle attack), and Comcast can’t snoop into what’s in the data that your company is sending to you before it delivers it to you.

Having a reliable, trustworthy connection to a server over the internet can be a very valuable tool. In a world of big data, hacking, online banking, password leaks, and government surveillance, being able to communicate with anyone securely is very important.
In addition to providing secure connections to remote servers, VPNs provide another incredibly useful ability as a sort of side effect — a VPN can act as a sort of ‘online mask,’ so that you can browse around a website without the website knowing exactly who you are. Generally speaking, your identity to the World Wide Web is your IP address, which can be used to determine your location down to the city/town. When you access a website, you send your IP address to the website’s server (so that the website knows who to send information back to), and your internet service provider (e.g. Comcast) knows that you are communicating with this website (if your connection is unencrypted, Comcast can also see the content of your communications with the website). When you access this website through a VPN server, your request first goes through the encrypted tunnel to the VPN server, and the VPN server then bounces the request along to the website itself (over an unencrypted connection). When the website responds to the VPN server, the server bounces the response back to you over your encrypted tunnel. The website believes that they are just communicating with the VPN server, without any clue that their response is being passed on to anyone else. Comcast may be able to read the communications between the website and the VPN server, but they have no way of knowing that the communication is connected to you.
There are other ways to hide your identity on the internet. You can use a proxy, which appears similar to a VPN on the surface. You can connect to a website through a proxy to hide your IP address from the website, so the proxy also acts like a man-in-the-middle like a VPN does. The difference is that your computer’s connection to the proxy is not encrypted, so from a large enough scope, your communication with the website could be traced back to you. If an internet service provider such as Comcast happened to service both the connection from you to the proxy server, AND from the proxy server to the website, they could piece together that it was you who connected to the website over the proxy, and since the communications aren’t encrypted, they could also see exactly what you were communicating about with the website over the proxy. Proxies also don’t mask your IP address over the entire computer — you have to configure each application individually to send all of it’s internet-based protocols through a proxy server. VPNs are OS-wide, meaning that it protects your entire computer no matter what internet-based protocol is being sent out.

Thanks to the ability to provide anonymity over the internet, some companies have emerged that make a business out of providing access to their VPN servers. Their business model is that, for a fee, you can connect to their VPN servers to use as an ‘online mask’ however you like, and whatever you do won’t be traced back to you. The catch is whether a particular company is trustworthy or not — some VPN service providers log your activity and give it to authority or sell it to the highest bidder, essentially nullifying the anonymity that a VPN provides. You should always be skeptical and selective when choosing a VPN service provider; and remember, you get what you pay for. There are many free VPN service providers out there that allow you to use their servers for free up to a certain bandwidth; as a general rule of thumb, whether it be regarding free VPN service providers or free social networks, as long as someone is making a profit, if you’re not paying for the product, YOU are the product!
In conclusion, there are many ways to protect yourself over the internet, and selecting the best tool for your needs is the way to go. If you’re abroad and you want to watch a show on Netflix but it’s not available in the country you’re in, you can use a proxy to connect to a US server and stream it over your proxy connection, since encryption isn’t mandatory for this case. If you’re at Dunkin’ Donuts and you’re working on a top-secret project for your startup and you don’t want any tech-savvy thieves stealing your code over your free Wi-Fi connection, you can use a VPN to encrypt your connection between you and your company server. If you want to check your bank account online, but the bank doesn’t have good online business practices and don’t encrypt their web communications by default, you may want to use a VPN when logging into your bank’s website to make sure that nobody successfully fishes for your username and password. And if you’re working on an absolutely, positively, unconditionally classified, top-secret, sensitive, need-to-know-basis document, but you really, really, really want to get a frappuchino, perhaps you should consider getting yourself one of those sweatshirts with the oversized privacy hoods that you can wrap around your computer display, as seen above.
